Innovating to Protect
Your Privacy
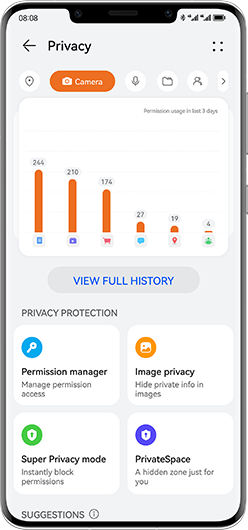
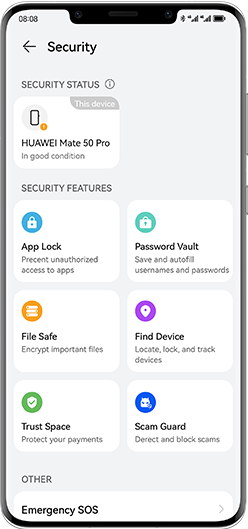
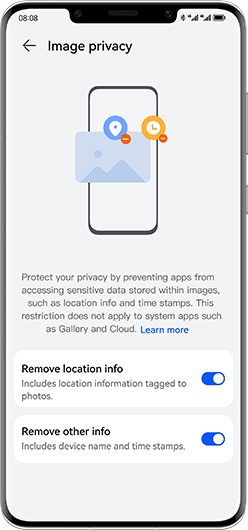
Your Privacy
Learn more>>
Prioritised Privacy Across Apps
More on App Security

HUAWEI Browser
Browsing Without Worries
HUAWEI Browser
HUAWEI Browser automatically identifies tracking websites and blocks tracking cookie
requests by default. It even disables API parameters that can identify user device fingerprints, to
reduce the chance that anyone could track you. During your web browsing, automatic attempts to open web
pages and download apps will be spontaneously blocked.

HUAWEI Health
Keeps Your Private Data Secure
HUAWEI Health
All personal data in Huawei Health is encrypted via a dedicated device-specific key,
and stored within the mobile app. This means that no other party, not even Huawei, can access the
encrypted data—and that it's entirely up to you how to use or share it.
HUAWEI AI Life
Steps In to Help,
Stays Out of Your Life
Stays Out of Your Life
HUAWEI AI Life
AI Life will only collect and process the data it absolutely needs to provide a
superior level of service. The data will be transmitted to HUAWEI Mobile Cloud via an encrypted channel
and encrypted for storage. When you unlink a device from AI Life, the device data will then be
automatically deleted from HUAWEI Mobile Cloud.

Celia
Listens In When Needed,
Tunes Out When Not
Tunes Out When Not
Celia
Celia only processes voice information after being awakened, and all AI Voice-related
personal data, such as voiceprint data and voice instructions, is processed only on the device. We only
collect the personal data that is absolutely necessary to provide services. The data will always be
transmitted in encrypted form, and will never be associated with your voice or location information or
used for location tracking or behavioural analysis.
Multi-layer Data Encryption on the Cloud
More on Cloud Security

HUAWEI Mobile Cloud
HUAWEI Mobile Cloud keeps important data, such as Gallery, Contacts, and Calendar,
under lock-and-key, from collection, to transmission to storage. It encrypts data at multiple layers, so
no one can ever access your data without your consent.
Find out more about
privacy and security.
privacy and security.
Four Proposals
●Top-down structure and process
●Airtight privacy and security framework
●Security verification framework co-developed with industry stakeholders
●Open security and privacy capabilities for ecosystem partners
●Airtight privacy and security framework
●Security verification framework co-developed with industry stakeholders
●Open security and privacy capabilities for ecosystem partners
Three Commitments
●Privacy is a fundamental user right.
●Data is encrypted on a comprehensive basis.
●Data is always kept entirely under the user's control.
●Data is encrypted on a comprehensive basis.
●Data is always kept entirely under the user's control.